How Secure is Your 5G Network?
New Challenges and Solutions in an Open, Disaggregated Cloud-Native World
Time to grab a cup of coffee, as I describe how the transition towards open, disaggregated, and virtualized networks – also known as cloud-native 5G – has created new challenges in an already-heightened 4G-5G security environment.
5G networks move, process and store an ever-increasing amount of sensitive data as a result of faster connection speeds, mission-critical nature of new enterprise, industrial and edge computing/AI applications, and the proliferation of 5G-connected IoT devices and data centers. At the same time, evolving architectures are creating new security threat vectors. The opening of the 5G network edge is driven by O-RAN standards, which disaggregates the radio units (RU), front-haul, mid-haul, and distributed units (DU). Virtualization of the 5G network further disaggregates hardware and software and introduces commodity servers with open-source software running in virtual machines (VM’s) or containers from the DU to the core network.
As a result, these factors have necessitated improvements in 5G security standards that include additional protocols and new security features. But these measures alone, are not enough to secure the 5G network in the cloud-native and quantum computing era. This blog details the growing need for cloud-optimized HSMs (Hardware Security Modules) and their many critical 5G use cases from the device to the core network.
Key HSM Applications in the 5G Network
Figure 1 below illustrates the application of HSMs (depicted as a LiquidSecurity 2 HSM photo) in the 5G network/ecosystem from connected end devices on the left to the back-end core network on the right. The key use cases explored in this blog, are as follows:
- 3GPP (3rd Generation Partnership Authentication Framework) with PQC (Post-Quantum Crypto)
- SIM/eSIM provisioning during manufacturing and OTA (Over-The-Air)
- Secure Communication (SSL/TLS/IPsec/MACsec)
- Code Signing for Software Intensive Environments
- Database/VM/Container Security
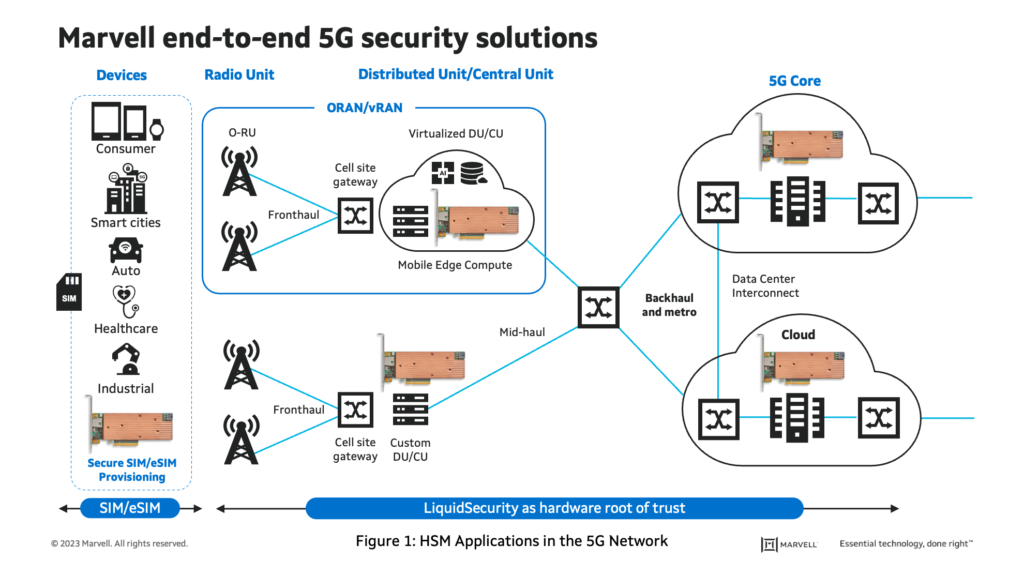
On the left of Figure 1, end devices either use a SIM (Subscriber Identity Module) card—the same small SIM cards we’re all use to getting from carriers like Verizon, T-Mobile, or AT&T—or an eSIM, which is an embedded IC version of a SIM card, like what’s being shipped now with all Apple iPhones. You’ll notice that, except for the China version, all newer iPhone’s no longer have a SIM port. SIM cards and eSIM IC’s all hold confidential information about the carrier, the end device, and the subsequent user. Because of this, security is very important.
All 5G enabled devices connect to the 5G network via the RU. The RU is a small box that sits atop cellular towers, buildings or antenna sites cleverly disguised as evergreen trees. It converts the radio signals into digital signals for transmission over packet networks.
The DU may sit very close to the RU, either at the base of the RU pole or several kilometers away in a data center. It uses specialized baseband hardware (with accelerators) running L1 functions, with standard COTS host servers and or transport processors/SmartNICs running L2/L3. In a major city or metro area, there may be a farm of DU’s, which is basically a building that houses multiple servers. The CU (or Central Unit) can be co-located with the DU or sit tens of kilometers away in a data center as a COTS server and/or accelerators handling the RRC (Radio Resource Control), SDAP (Service Data Adaptation Protocol), and PDCP (Packet Data Convergence Protocol) layers. In the OSI model, it’s upper L2 and L3. It’s also where edge computing capabilities like data analytics and AI/ML inferencing may be located. The CU communicates with the DU via copper or fiber. And these functions can be run in on-prem datacenters or offered as a service from Cloud Service Providers (CSPs).
And finally, the CU connects to the core network over the back-haul link. The core network is the heart of the carrier’s internal network. Subscriber, billing, SIM/eSIM provisioning information, and databases containing PII (Personally Identifiable Information) are a few examples of sensitive data contained in the core network. This can be on-prem or in the cloud.
HSMs can be used as the Root-of-Trust, underpinning the security from the 5G devices to the Core Network itself.
A Quick Primer on HSMs
An HSM is a physically secure computing device that safeguards and manages digital keys, performs encryption/decryption functions, and provides strong authentication mechanisms. They typically come in two form factors, a PCIe card or a 1U network attached server. HSMs are certified against NIST (National Institute of Standards and Technology) standards, the latest/highest level of compliance being FIPS 140-3. Most HSMs provide tamper evidence (visible signs of tampering), tamper resistance (the HSM becomes inoperable upon tampering) or tamper responsive (deletion of keys upon tamper detection). All provide logging and alerting features, strong authentication, and key management features, and support common API’s like PKCS#11.
The first HSM was built in 1973 by Mohammed Atalla, entitled the Atalla box, which was used for ATM transactions. Although initially targeted towards the payment market, HSMs are now the de facto standard for managing encryption keys for a variety of use cases. They are now the root-of-trust in a much bigger ecosystem wheel. PKI (Public Key Infrastructure), many databases, most data lakes, VM’s, containers, audit logs, CA (Certificate Management) solutions, and IAM (Identity and Access Management) software all integrate with HSM’s to secure data-at-rest, secure data-in-motion, secure microservices as they spin up and down, or secure encrypted audit logs. Just think of HSMs as a physically secure vault for your encrypted data in an ever-increasing hostile environment.
5G Use Cases for HSMs
The five (5) main use cases for HSMs within the 5G ecosystem are:
1. 3GPP (3rd Generation Partnership Authentication Framework) with PQC (Post-Quantum Crypto)
The standard requires the use of IPsec communication based on pre-shared keys or digital certificates issued from PKI (Public Key Infrastructure) systems. HSM’s are used in digital certificates and PKI systems to ensure that the private key in a public/private key-pair is secure.
With the introduction of quantum computers, the requirement for NIST certified PQC algorithms is now mandatory to thwart brute force attacks from these newer powerful computers. Until NIST ratifies these algorithms as part of the NIST FIPS 140-3 certification process, HSM vendors will need to be flexible in their support. HSM vendors need to support “crypto agility,” or the ability to quickly incorporate these new NIST certified PQC algorithms in subsequent software updates. This requires an HSM with sufficient performance headroom for future flexibility to accommodate an evolving set of security standards.
2. SIM/eSIM provisioning during manufacturing and OTA (Over-The-Air)
SIM cards or eSIM chips are provisioned during manufacturing and then “reprovisioned” in the field through a framework called SUPI (Subscription Permanent Identifier)/SUCI (Subscription Concealed Identifier).
Secure manufacturing is a relatively new use case for HSM’s, even though manufacturing had moved to 3rd party overseas companies decades ago. Manufacturers are now provisioning software, firmware, adding unique IDs, and certificates during the manufacturing process of IOT devices. Because of this, the attack vector for a hacker is now the manufacturing facilities. And authentication-related keys can be compromised during SIM personalization and provisioning. HSMs provide a physically secure solution to a potentially hostile manufacturing environment, to generate and store keys, certificates, or unique ID’s. Just think of SUPI as a unique identifier given to each subscriber or user by the network provider. In 3G/4G, this ID was sent in plaintext over the radio access link. This allowed hackers to identify the user, locate and track them, and spoof their SIM. In 5G, the addition of the 3GPP specification called for the use of ECC (Elliptic Curve Cryptography) algorithms, which are more secure, but don’t require tremendous CPU horsepower. Using a public key from the home network provider, stored inside the SIM, and ECC Algorithms, the SUPI is cryptographically concealed. This new sealed SUPI is known as SUCI (Subscription Concealed Identifier).
This mitigates any potential man-in-the-middle attacks, because the SUPI is wrapped/encrypted with a public key provided by the home network provider. The private key managed by the home network provider is then used to unwrap/decrypt the SUCI to grab the SUPI values. This public/private key pair is generated and managed within an HSM.
3. Secure Communication (SSL/TLS/IPsec/MACsec)
The communication process between the front-haul, mid-haul, and back-haul happens over SSL (Secure Socket Layer), TLS (Transport Layer Security), IPsec (Internet Protocol Security), or MACsec (Media Access Control Security) secure communication protocols. These encryption protocols use encryption keys that can be generated and managed within an HSM, or crypto accelerator card.
4. Code Signing for Software Intensive Environments
Personally, I think code signing is cool. Think of code signing as a tamper resistant cap on a medicine bottle. Would you take a pill from a bottle that had a broken seal? Of course not. Similarly, you wouldn’t you run a piece of software on your computer that may have been tampered with and injected with a virus. So how can you tell that the MacOS software running on your Apple laptop is from Apple? Code signing is how companies protect their software from hackers.
Software developers and publishers sign their code using the private key corresponding to their registered digital certificates. The certificates bind the identity of the developer/publisher to an asymmetric key pair. The private key component of the key pair is used to digitally sign a shortened version of the code, aka a hash. The consumer of the software uses the associated public key to verify the signature. The signed hash provides validation of who the developer/publisher are and confirmation that the code has not been altered since it was signed.
Properly managing the private key is the root-of-trust for any signature system. If compromised, it allows an attacker to alter and sign the software themselves, which could be injected with malware or a virus. HSMs are used to generate and manage the public/private key pair. And since 5G uses open-source software, code signing across the entire ecosystem is very important.
5. Database/VM/Container Security
As I previously stated, HSMs are a small cog in a much bigger ecosystem wheel. Most databases (Oracle, NetApp, Microsoft SQL), datalakes (Snowflake, Cloudera), VM’s (VMware), Containers (Kubernetes, RedHat), Audit Logs (Splunk), and Certificate Management solutions (Venafi), all integrate with HSMs to secure data at rest, secure microservices as they spin up and down, or secure encrypted audit logs. The different software services typically connect to HSMs via common API’s like KMIP (Key Management Interoperability Protocol) and PKCS#11 (Public-Key Cryptography Standards).
Using HSM’s to manage encryption keys can help better protect enterprise-wide encryption for VMware customers’ private data in vSAN and vSphere environments. This helps ensure that users remain in control of their encryption keys and data secrets. The encryption keys remain more secure within the HSM, even if attackers have physical access or root credentials to the key management server.
K8s (Kubernetes) operates two realms commonly known as the data and control planes. K8s relies on internal secrets for bootstrapping various critical services in the control plane to ensure trust. These secrets are stored in the “etcd database” and are base64 encoded. HSMs can encrypt the entirety of the “etcd database” on behalf of Kubernetes to ensure data-at-rest security.
Marvell’s LiquidSecurity HSMs are already deployed at the top five CSPs to offer HSM services in the cloud for thousands of customers globally. Our recently announced LiquidSecurity 2 HSM provides unparalleled performance, crypto agility (support for the latest PQC algorithms), and cloud optimized features. It can be deployed on-prem or offered as a service in the cloud within the edge compute CU or backend core network. All five use cases discussed in this blog can make use of Marvell HSMs to secure the encrypted 5G datasphere from edge to core.
Okay, well maybe that was more than just one cup of coffee!
HSMs are adapting and growing to support newer markets and newer threat vectors in the quantum computing era. And crypto algorithms are only as good as the management and access of the keys used to encrypt/decrypt the data. In a “Zero Trust” world, HSMs should always be used as the “Root-of-Trust.”
This blog contains forward-looking statements within the meaning of the federal securities laws that involve risks and uncertainties. Forward-looking statements include, without limitation, any statement that may predict, forecast, indicate, or imply future events or achievements. Actual events or results may differ materially from those contemplated in this blog. Forward-looking statements speak only as of the date they are made. Readers are cautioned not to put undue reliance on forward-looking statements, and no person assumes any obligation to update or revise any such forward-looking statements, whether as a result of new information, future events or otherwise.
Tags: 3GPP, 5g, 5G datasphere, 5G enabled devices, 5G network security, 5G security environment, cloud-optimized HSMs, crypto accelerator card, crypto algorithms, HSM Applications, HSM services, HSMs, O-RAN standards, Post-Quantum Crypto, Secure Communication, Virtualization of the 5G network, vSAN, vSphere

